WiseCleaner Think Tank
Encounter difficult computer problems?
All about maintenance and optimization of your Windows System.
May 30, 2025
Downloading files from the internet is a common part of everyday computer use, but not all files are safe. Malicious software can hide in seemingly harmless documents, installers, or media files, posing a serious threat to your privacy, data, and system integrity. This guide will walk you through essential steps to check if a downloaded file is safe before opening or executing it.
The best way to avoid malware is to avoid downloading it in the first place. Trusted sources have stronger security policies, verified uploads, and are less likely to host dangerous files.
Only download software or files from the developer’s official website or well-known platforms like Microsoft Store, GitHub, Ninite.
Windows SmartScreen and other built-in protections help prevent malicious or unverified apps from running. Disabling them exposes your system to unnecessary risk.
Keep Windows SmartScreen Enabled helps block unrecognized or potentially harmful apps. When a warning appears, don’t rush to bypass it. Instead, stop and investigate the file or search for user feedback online. SmartScreen isn’t perfect—but it’s usually right when it raises a flag.
Before opening a file, you should always perform a security scan to detect hidden malware. Windows Security (formerly Windows Defender) offers real-time protection for free.
Right-click the downloaded file and select Scan with Microsoft Defender. It takes only a few seconds and can detect known malware or suspicious patterns.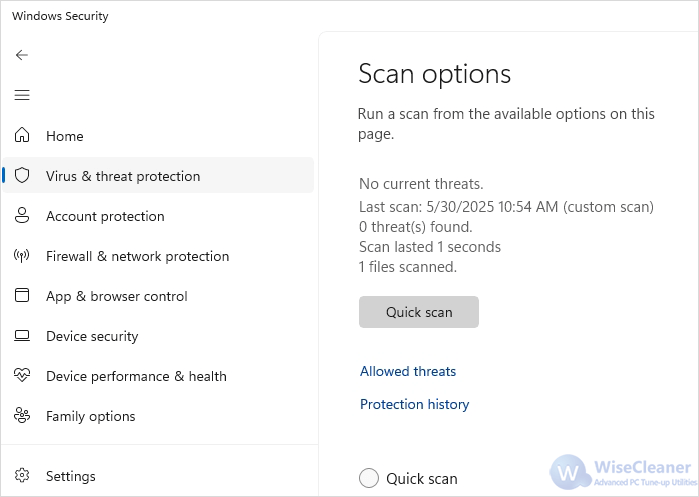
File extensions reveal the file type. Attackers sometimes hide malware in files that pretend to be harmless documents or images by manipulating the file name.
Open File Explorer and go to View > Show > File name extensions. This helps you catch deceptive names like xxx.pdf.exe, which would otherwise just appear as xxx.pdf. Executable formats (.exe, .bat, .cmd, .js, .vbs, and .msi) can run code on your system. Be especially cautious with these—don’t open them unless you’re 100% sure of the source.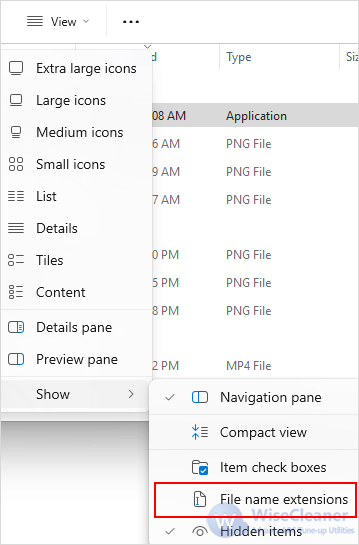
A valid digital signature confirms that a file was published by a legitimate developer and hasn’t been tampered with. Unsigned executables should raise caution.
Right-click the file > Properties > Digital Signatures tab. Legitimate software often has a valid signature. If there is no signature, proceed with more caution.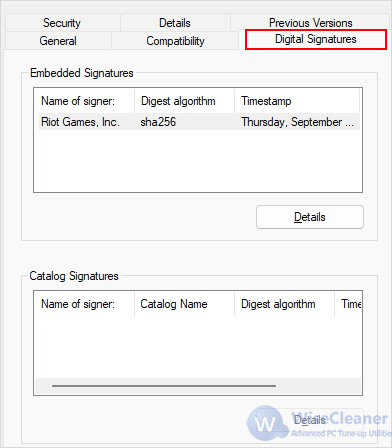
A file hash acts like a fingerprint. Even a tiny change to a file (e.g., from a virus) changes its hash value. Comparing it with the hash provided by the official site ensures the file hasn’t been altered.
Open PowerShell and run:
Get-FileHash "file path"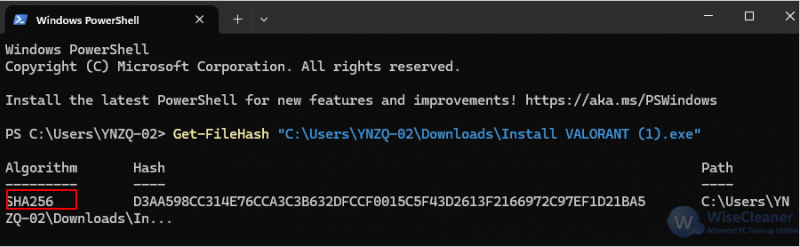
If the software vendor provides a hash on their website, compare it to the one you computed. A mismatch means the file may be corrupted or tampered with.
A sandbox creates an isolated environment to safely test files, preventing them from affecting your main system—even if they turn out to be malicious. For more information on how to enable Sandbox and test for potentially unsafe programs, you can refer to this article.
Being cautious with downloaded files is essential to keeping your system and data secure. A combination of good download habits, scanning tools, and common sense goes a long way. When in doubt—don’t open the file. It’s better to be overly cautious than to risk a malware infection.
wisecleaner uses cookies to improve content and ensure you get the best experience on our website. Continue to browse our website agreeing to our privacy policy.
I Accept